Close your IoT attack surface gaps
Safe today. Safe tomorrow.
Lightweight Security
POST-QUANTUM PROTECTION
NIST COMPLIANT

Protect Commercial And Government Customers From Current And Future Cybersecurity Attacks

Secure Iot Devices And Data In Transit To Reduce A Rapidly Expanding Attack Surface

Patented Lightweight Security Plus Data Analytics Enables CISOS To Get Ahead Of Cyberattacks
Billion
%
IoT Devices
NOT PROTECTED
%
Companies
Read AgilePQ’s position papers on the most recent cybersecurity attacks
Million
DIRECT COST PER BREACH
%
surge
in IoT attacks in 2020
trillion
GLOBAL CYBERCRIME COST IN 2021
IOT security Challenges
IoT Device Limitations Hamper Security
Because IoT devices have small processors, limited memory, and low power consumption, current IPSec security and encryption methods developed more than 20 years ago cannot work on small IoT devices.

There is no security solution for Class 0, Class 1, and Class 2 devices beyond seeing them on your network and reacting to threats when they occur.
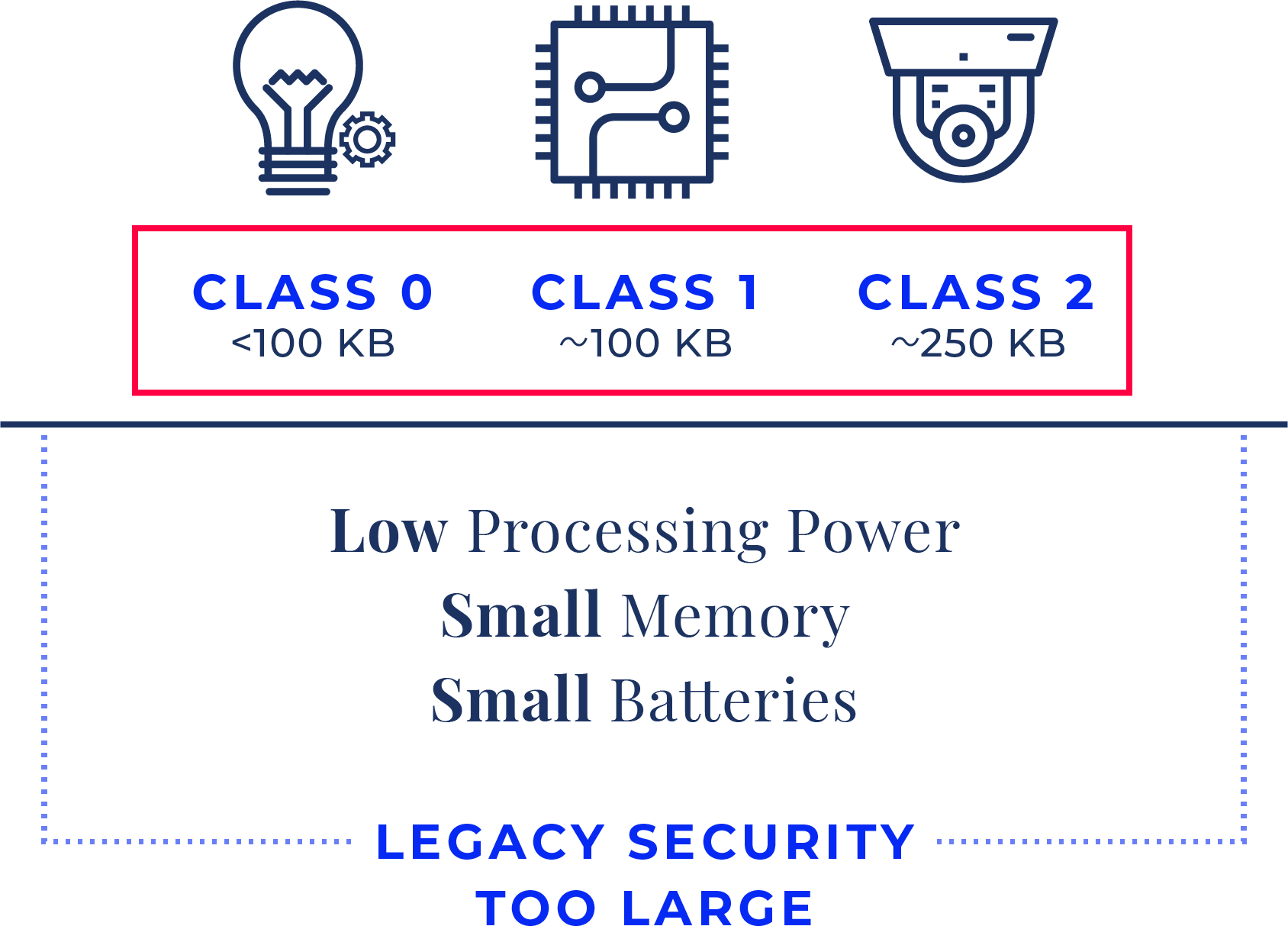

The Internet Engineering Task Force (IETF) classifies connected, small IoT devices into three categories according to processing ability, memory size, and power consumption. While IPSec security works on large devices not classified by IETF (smartphones to servers), it does not work on IoT (Class 0 – 2) devices because the code size and compute power necessary simply don’t fit given limited CPU and RAM resources.
Solutions
SLiM
Cipher Suite
After years of research and development, AgilePQ has developed the Secure Last IoT Mile (SLiM) Cipher Suite. The patented solution secures data in transit by using a key server that is optimized for a very small encryption algorithm installed on the IoT devices. In fact, AgilePQ’s code footprint is 1,000 times smaller than the IPSec standard developed more than 20 years ago. By reducing the code size, the company was able to increase its key space to 256! with an overall footprint that is 1,000 times smaller. In addition, the larger key space makes it 400+ times more secure than today’s standards.

NIST COMPLIANT
NIST’s Cybersecurity for the Internet of Things (IoT) program supports the development and application of standards, guidelines, and related tools to improve the cybersecurity of connected devices and the environments in which they are deployed.
POST-QUANTUM PROTECTION
Quantum computers will soon break the IPSec encryption methods developed more than 20 years ago. This puts encrypted data at risk. AgilePQ protects against current and future attacks by increasing encryption 256! (400+ orders of magnitude more secure).
LIGHTWEIGHT SECURITY
AgilePQ enables you to know what’s on your network, detect threats on IoT devices, manage the devices, and gain insights to make informed decisions about your IoT device security, all while intercepting and stopping threats to all data in transit.
Enterprises and government organizations now have a lightweight solution to secure even the most constrained IoT devices.
SLiM Lightweight Cipher Suite – Differentiated Features
LPQ256!
<2.4KB (1,000 times smaller)
1
256! (400+ orders of magnitude larger key space)
2
Up To 80% battery savings
Up to 10 times faster processing speeds
1/10TH data to connect to TLS
Adaptable block size (any size)
Yes
>3000KB
>100
32 Bytes
14
Standard TLS connection
Solutions
NIST Compliant
NIST’s Cybersecurity for the Internet of Things (IoT) program supports the development and application of standards, guidelines, and related tools to improve the cybersecurity of connected devices and the environments in which they are deployed.
The SLiM Cipher Suite is fully NIST compliant, so you can protect your IoT devices, detect nefarious activities, respond to threats, recover from disruptions, and identify the cause of attacks.
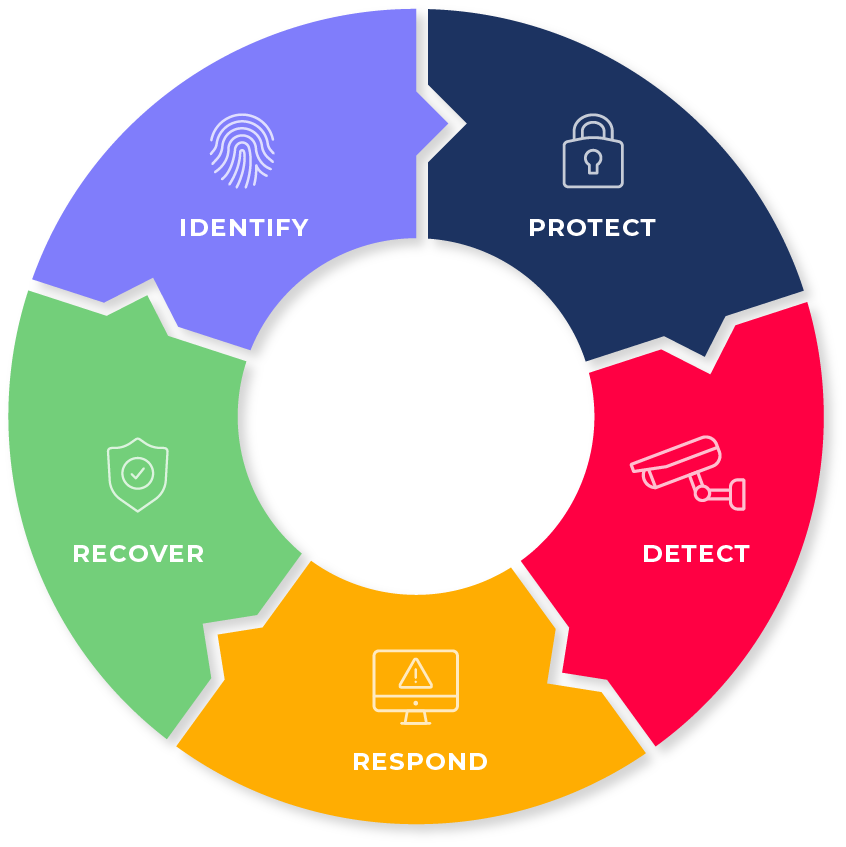
SOLUTIONs
Post Quantum
Unlike today’s servers, laptops, and smartphones that only process one command at a time, quantum computers process millions of commands simultaneously. This capability enables them to break the protection currently used on devices that hide transmitted data using encryption.
The SLiM Cipher Suite protects IoT devices from current and future threats, even quantum computing attacks by increasing each message key to 288 bytes versus the 32-byte key size used in standard messaging today. This means that the time or space required to solve its massive key space is intractable and infeasible given physical limitations of quantum processors.
SOLUTIONs
Device Visibility and Analytics
With device visibility and analytics, AgilePQ enables you to know what’s on your network, manage the devices, and gain insights to make informed decisions about your IoT device security.



Whitepapers
Colonial Pipeline Co. Ransomware Attack
Whitepapers
Consequences and Risks of Security Breaches from IoT Devices
Whitepapers
A Guide to Post-Quantum Security for IoT Devices
Whitepapers
SLiM Security for Cellular, Satellite, and Constrained Networks

Get In touCh
Schedule a
demo today.
Seeing is believing. With AgilePQ, you’ll turn your IoT devices from a corporate liability into a quantum-safe, NIST compliant, security solution.
Safe today. Safe tomorrow.
10653 River Front Parkway, Suite #140
South Jordan, UT 84095
833.244.5377
Info@agilepq.com
